Palm Vein Pattern
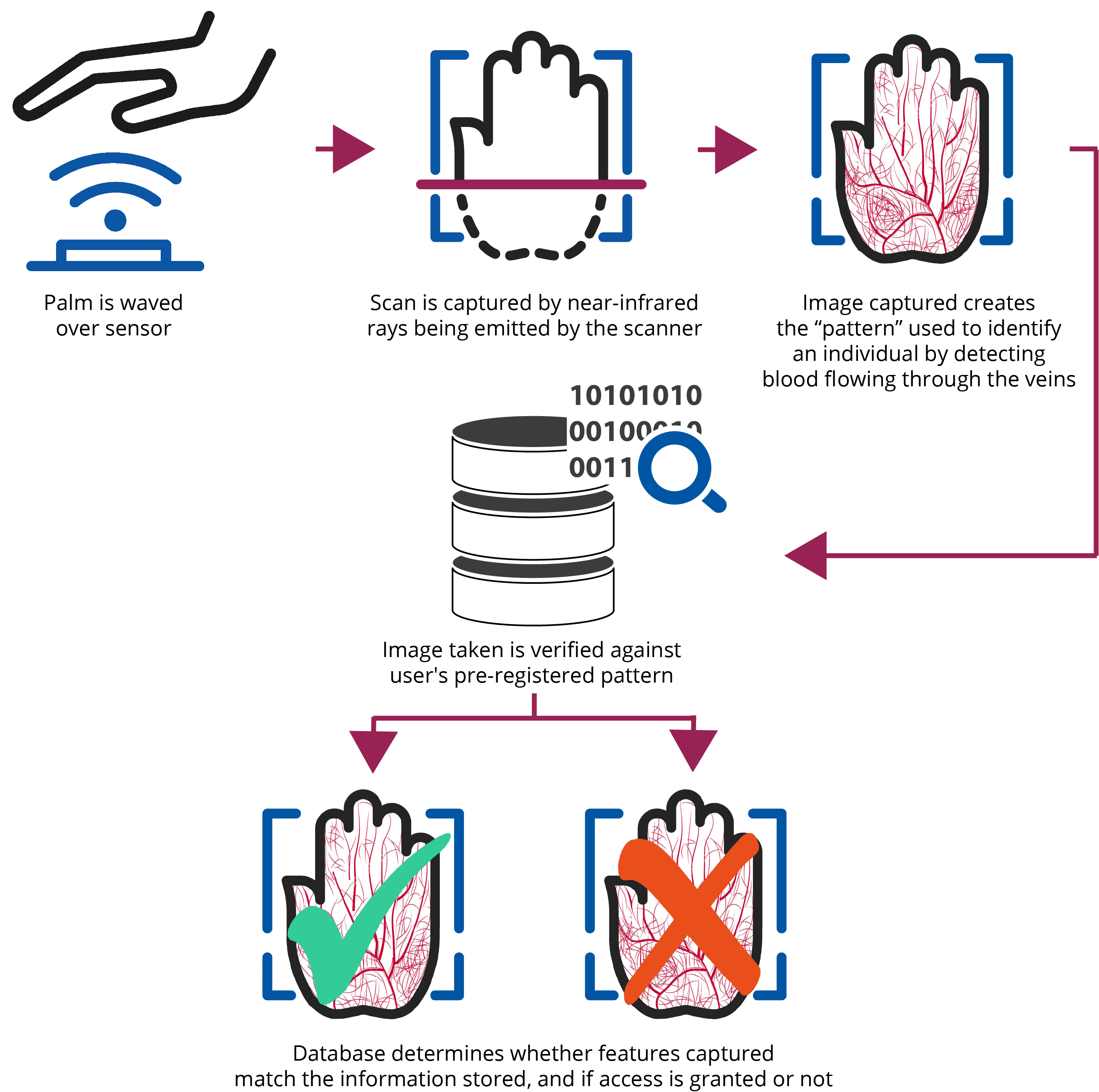
Palm Vein Pattern - Web palm vein scan is a powerful, relatively new biometric that uses the internal vein pattern of your palm to identify you. How will palm vein patterns be used and stored? Palm vein recognition exhibits high security, as it uses the network of blood vessels underneath palm skin for recognition. How will palm vein patterns be used and stored? It is a highly secure technology because palm vein pattern is information contained within the body of someone. This enhances the level of security and reliability of palm scanning as an authentication technology. Therefore, the move by these payment. Candidates simply place a hand on the device containing the sensor, which records the pattern of their palm veins on a digital template. Web what is palm vein recognition? Similar to fingerprint, each person's palm vein pattern is unique and doesn't change. Palm vein recognition exhibits high security, as it uses the network of blood vessels underneath palm skin for recognition. This enhances the level of security and reliability of palm scanning as an authentication technology. Web palm vein recognition scans the veins inside of a candidate’s hand and creates a digital template that represents their unique vein pattern. Author links open overlay panel. Web palm vein patterns are hidden inside the human's body and, therefore, should be difficult to capture without a person knowing it. Similar to fingerprint, each person's palm vein pattern is unique and doesn't change. Moreover, encryption of the data makes it less susceptible to being compromised. Web palm vein scan is a powerful, relatively new biometric that uses the internal vein pattern of your palm to identify you. Towards the generation of synthetic images of palm vein patterns: As palm vein is interior biological information of the body, vein patterns are much harder for intruders. Web vein matching, also called vascular technology, is a technique of biometric identification through the analysis of the patterns of blood vessels visible from the surface of the skin. Towards the generation of synthetic images of palm vein patterns: Similar to fingerprint, each person's palm vein pattern is unique and doesn't change. Combining the palm print and vein patterns. ,. A biometric technology that authenticates users on the basis of vein pattern recognition rather than iris scans or fingerprint readers. This scan produces a unique biometric template that is a digital representation of the patient’s unique vein pattern. Web palm recognition is set to become the industry standard for biometric payments, writes arnie cho. , marco mora d e. The. Web palm scanning uses the vein patterns in a person's palm print for personal identification. Web palm vein recognition scans the veins inside of a candidate’s hand and creates a digital template that represents their unique vein pattern. Web vein matching, also called vascular technology, is a technique of biometric identification through the analysis of the patterns of blood vessels. It utilizes the unique patterns of veins which people have in their palms to serve as a means of personal identification. The fact that law enforcement can collect fingerprints to identify suspects at the scene of a crime highlights the vulnerability of this biometric. Candidates simply place a hand on the device that holds the sensor, which records the pattern. Web palm vein authentication uses vein patterns on the palm of a person as personal information. The pattern of veins is set for life before a person is even born, by 14 weeks of gestation, and is. How will palm vein patterns be used and stored? Web palm vein recognition exhibits high security, as it uses the network of blood. Therefore, the move by these payment. Similar to fingerprint, each person's palm vein pattern is unique and doesn't change. Web palm recognition is set to become the industry standard for biometric payments, writes arnie cho. , marco mora d e. Ity for the nclex® exam program. Combining the palm print and vein patterns. A biometric technology that authenticates users on the basis of vein pattern recognition rather than iris scans or fingerprint readers. The pattern of veins is set for life before a person is even born, by 14 weeks of gestation, and is. Fingerprints can be collected by a third party without your consent. Therefore,. Similar to fingerprint, each person's palm vein pattern is unique and doesn't change. Therefore, the move by these payment. Web palm vein scan is a powerful, relatively new biometric that uses the internal vein pattern of your palm to identify you. This enhances the level of security and reliability of palm scanning as an authentication technology. The palm scanner creates. Web palm vein scanning, an advanced biometric technique, captures and analyses the intricate patterns of veins in an individual’s palm. The fact that law enforcement can collect fingerprints to identify suspects at the scene of a crime highlights the vulnerability of this biometric. The palm scanner creates an image of vein patterns in the hand and then compares them to. Web palm vein authentication uses the blood vessel patterns of the palm vein in the subcutaneous tissue of the human body to discriminate between individuals. The fact that law enforcement can collect fingerprints to identify suspects at the scene of a crime highlights the vulnerability of this biometric. The palm scanner creates an image of vein patterns in the hand. Moreover, encryption of the data makes it less susceptible to being compromised. Therefore, the move by these payment. As palm vein is interior biological information of the body, vein patterns are much harder for intruders. Web palm scanning uses the vein patterns in a person's palm print for personal identification. The fact that law enforcement can collect fingerprints to identify suspects at the scene of a crime highlights the vulnerability of this biometric. Towards the generation of synthetic images of palm vein patterns: Web palm vein scanning, also known as palm vein recognition, is a modern authentication technology based on biometrics. Author links open overlay panel. Palm vein recognition exhibits high security, as it uses the network of blood vessels underneath palm skin for recognition. Web palm vein recognition scans the veins inside of a candidate’s hand and creates a digital template that represents their unique vein pattern. The palm scanner creates an image of vein patterns in the hand and then compares them to others in the database. Web palm vein scanning, an advanced biometric technique, captures and analyses the intricate patterns of veins in an individual’s palm. It is a highly secure technology because palm vein pattern is information contained within the body of someone. Web palm vein authentication uses the blood vessel patterns of the palm vein in the subcutaneous tissue of the human body to discriminate between individuals. Similar to fingerprint, each person's palm vein pattern is unique and doesn't change. Web what is palm vein recognition?Will Palm Vein Patterns the New Identification? Different Truths
A schematic diagram wrist and palm vein verification framework (see
Palmvein images in the database of this study. Download Scientific
The benefits of palm vein identification Argus TrueID
Palm vein recognition with local texture patterns Mirmohamadsadeghi
Iris recognition Biometrics Vs Palm Vein Biometrics
How biometric palm scans help keep hospitals secure CBS News
(PDF) 3D Ultrasound palm vein pattern for biometric recognition
Review of palm vein recognition Wu 2020 IET Biometrics Wiley
Low‐cost biometric recognition system based on NIR palm vein image Wu
A Biometric Technology That Authenticates Users On The Basis Of Vein Pattern Recognition Rather Than Iris Scans Or Fingerprint Readers.
In Most Systems Using Vein Pattern Recognition, The Vein Pattern Is Stored As An ‘Image’ And May Or May Not Be Encrypted.
Web Palm Vein Patterns Are Hidden Inside The Human's Body And, Therefore, Should Be Difficult To Capture Without A Person Knowing It.
This Enhances The Level Of Security And Reliability Of Palm Scanning As An Authentication Technology.
Related Post: